qkd.lumii.lv
The Butterfly Protocol
by Institute of Mathematics and Computer Science, University of Latvia
Our original Butterfly Protocol is intended to provide Quantum Key Distribution (QKD) as a Service for non-QKD-capable clients.
Papers to cite:
- J.Viksna,S.Kozlovics,E.Rencis. Integrating Quantum Key Distribution into Hybrid Quantum-Classical Networks, 2023 [Download BibTeX]
- S.Kozlovičs, K.Petručena, D.Lārinš, J.Vīksna. Quantum Key Distribution (QKD) as a Service and Its Injection into TLS, 2023 [Download BibTex]
- SUBMITTED: The Butterfly Protocol: Secure Symmetric Key Exchange and Mutual Authentication via Remote QKD Nodes (2026)
QKD as a Service (QaaS) allows the users to securely obtain a shared secret from two remote key distribution centers (KDCs) running QKD equipment. QaaS uses a mix of quantum and classical channels in a way that is sustainable for active attacks on any single communication segment. The following figure illustrates the main components participating in QaaS from the end user point of view:
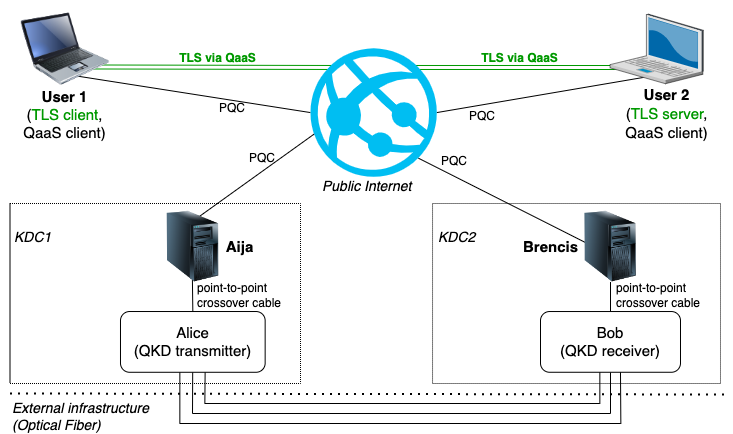
User 1 and User 2 (also known as the TLS client and TLS server) are end users of QaaS. They aim to establish a secure TLS connection (green) using a quantumly shared key. Since neither of the end users has direct access to QKD devices, each of the users connects to both KDCs (represented by the Aija and Brencis servers) using classical links encrypted using PQC algorithms (currently, we use FrodoKEM and SPHINCS+). KDCs return material that can be used to reconstruct the quantumly shared key that has been distributed using QKD devices between KDCs. An essential property of QaaS is that the full shared key is never transmitted via any single classical communication segment.
We will update the documentation and the code base soon. The code will be much easier to use and install.
In order to connect to our QaaS service, you will need the following:
- The QaaS user library, available at https://github.com/LUMII-Syslab/qkd-as-a-service (under
userlib+pqproxy). - Sample source code for User 1 and User 2 that connect using our TLS variant with QaaS and QKD support (implemented in the QaaS user library):
userlib+pqproxy/src/test/java/lv/lumii/test/QkdTestUser1.javafor User 1 (the TLS client);userlib+pqproxy/src/test/java/lv/lumii/test/QkdTestUser2.javafor User 2 (the TLS server).
-
These files (can be obtained upon request by mailing to syslab_services at lumii.lv):
ca.truststore- the root CA certificate used to validate QaaS servers Aija and Brencis, as well as the User 1 client certificate and the User 2 server certificate;client.pfx- User 1 key and certificate (signed by the root CA) in the PKCS#12 format; used to authenticate User 1 at Aija, Brencis, and User 2;server.pfx- User 2 key and certificate (signed by the root CA) in the PKCS#12 format; used to authenticate User 2 at Aija, Brencis, and User 1;- the
qkd.propertiesconfiguration file, where key stores, passwords, as well as Aija and Brencis URLs are specified.
Upon request, keys and certificates can be generated using IDQ Quantis QRNG devices. All certificates (CA, client-side, and server-side) are based on the quantum-resistant SPHINCS+ algorithm.